
Business-critical applications must be up to date to ensure they continue providing the right insights at the right time while maintaining data, access and application delivery security.
In our first article in this series, we introduced XOps as the future for setting up and running production business applications at scale. Tredence’ s XOps offering provides a combination of cross-skilled people, strong partnerships, and the right accelerators for each point in the production business process value chain.
In the second article in the XOps series, we focused our attention on BizOps. BizOps is the core of the XOps process. All decisions and key insights come from business applications, and ensuring the stability, resilience and predictability of these applications forms the crux of BizOps. We illustrated BizOps in the context of a Trade Promotion Effectiveness (TPE) use case.
In this article, we continue down the rabbit hole and zoom into DevSecOps. Critical business applications need to constantly be kept up to date to ensure they continue delivering relevant insights to business stakeholders. Further, process and application delivery security need to be preserved, to ensure the confidentiality, integrity, accessibility, and regulatory compliance of the applications are maintained.
What changes after an application is live?
Once a solution/application goes live, several challenges come up in ensuring the entire process runs seamlessly resulting in more time and resources being spent. Some of these challenges are listed below:
- Troubleshooting and recovering from business disrupting application failures: The issues detected can often take days/weeks to fix and problems are often only discovered after the solution is running in production.
- Protection against performance issues: Proactively ensuring data center migrations, consolidation, expanded deployments, new releases and new users are protected from application performance issues.
- Executive and Business Level Reporting: Application performance is not a single group’s responsibility and has broad implications across IT operations, application teams and business owners. Alerts and notifications need to be enabled to all the relevant stakeholders if there is any impact on performance.
Reactive vs. proactive approach to application performance
With a reactive approach, the action is not initiated until an incident occurs. This does not necessarily mean that a breach has occurred; it simply means that some unusual or threatening activity has triggered an alert. Once alerted, the company’s incident response plan is initiated; in the beginning, the goals are to contain the threat and restore service.
With a proactive approach, organizations try to detect potential threats before an incident occurs. A proactive approach also includes regular, planned hunting exercises to detect threats that may be lurking in the system but not yet detected or perhaps not yet triggered.
Critical business applications need to constantly be kept up to date to ensure they continue delivering relevant insights to business stakeholders.
Why are application versioning and security important?
Multiple developers are usually involved while developing an application or a solution, each working on different elements, features, and components. In such a scenario, it’s a mandate to manage all the different environments and versions on which the application or solution is developed.
It’s critical to maintain proper coordination between all these varied components so that the final product isn’t plagued by chaos, conflicts, and security defects. This is where a version control system comes into the picture. It will track all the activities of the developers involved, what they do on side branches, and help them resolve conflicts and fix high-risk vulnerabilities before pushing out their work to the final branch.
DevOps, though, has dramatically changed the DevSecOps velocity and frequency. We are talking just weeks or days per iteration. Existing compliance monitoring and security tools weren’t built to keep up with the rapid pace of change DevOps requires. If security models aren’t modified to keep up with the new expectations, a security catastrophe looms.
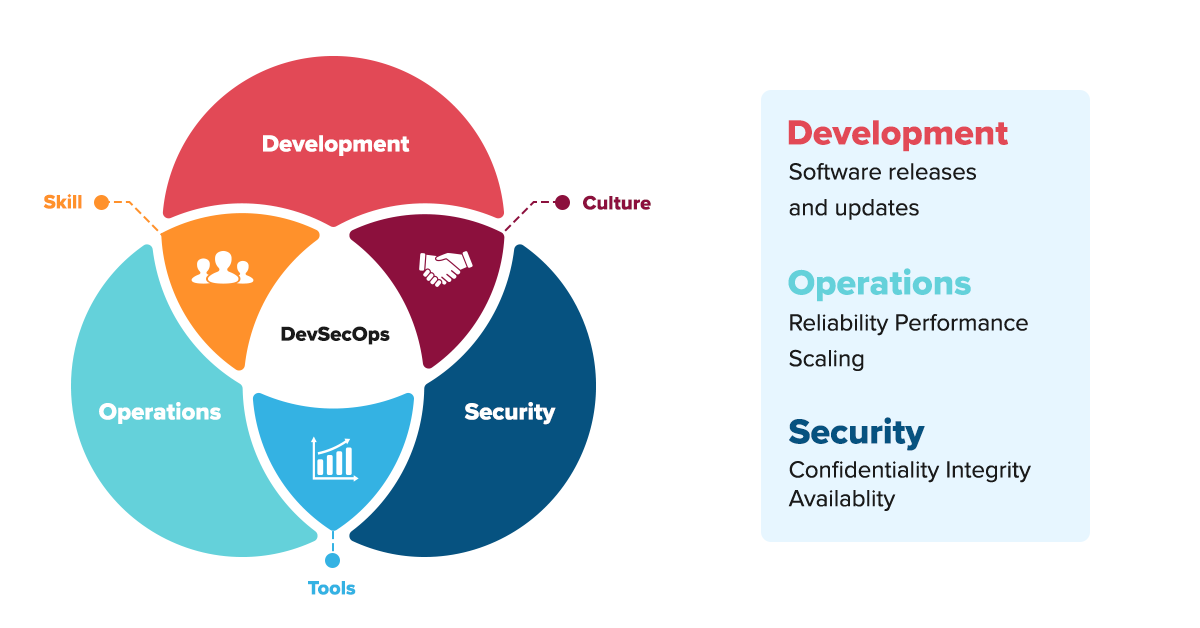
Why DevSecOps?
Today, no one will deny the importance of DevSecOps in ensuring the security and stability of their enterprise applications. In a nutshell, DevSecOps helps organizations deliver more secure software faster. Bugs and vulnerabilities can be identified early on in the development process, which can substantially reduce the development time. Other tangible benefits of this agile methodology include:
- Proactive security, which translates to better consumer trust
- Adaptability, which translates to scalability for organizations
- Better resource management, which translates to cost-efficiency
DevSecOps approach helps shift security processes to the start of the development cycle. Security issues are addressed as soon as they emerge. Thus, potential vulnerabilities are addressed at the very early stages of development cycles before additional dependencies creep in.
What is DevSecOps and why is DevSecOps important and relevant in the current digital-first market?
DevSecOps is DevOps with security built-in, right from the start. It means building security into requirements, into the design, the code, and the deployment stages — in short, into your entire DevOps pipeline. Older security practices tend to slow down development teams and with the time to market getting shorter every year, software development teams had to find a way to speed up their software development process without compromising on security. The goal of DevSecOps approach is to bridge security teams and developers while ensuring fast and safe delivery of code.
Things to focus on while implementing DevSecOps:
- Introduce security throughout the software development lifecycle to minimize vulnerabilities in software code.
- Ensure the entire DevOps team, including developers and operations teams, share responsibility for following security best practices.
- Enable automated security checks at each stage of software delivery by integrating security controls, tools, and processes into the DevOps workflow.
Note: With the advent of DevSecOps and the more recent BizOps, the focus has shifted to the growing importance of engaging continuously with CXOs of an organization to build a successful digital transformation journey.
It is important to note that the impact of DevSecOps and BizOps revolves around people. Leadership buy-in is thus key to ensure that the ops processes are adopted and implemented by larger organizations.
“Hardware and software should be treated together, integrated with cybersecurity early and frequently.”
In conclusion
Tredence’s Solutions Support practice helps organizations set up vertical and functional-specific business processes the right way – through a rigorous design and a scaled mindset – by bringing in decades of use-case expertise coupled with technical smartness. This is combined with a strong DevSecOps process and approach ensuring these processes continue to provide value over time.
If you want to understand how your business-critical process can be set up and maintained the right way, check out www.tredence.com or write to us at marketing@tredence.com to discuss further.

AUTHOR - FOLLOW
Vinit Doshi
Senior Manager
Topic Tags




